


If you're worried about the arcane nature of firewalls, don't be. A firewall simply enforces a set of rules as to what sort of traffic may pass through the firewall either from you to the internet, or from the internet to you.
If you are using a Windows XP machine as your gateway to the internet (connected to the cable or ADSL modem), I should mention that Microsoft's Internet Connection Firewall (http://www.pcmag.com/article/0,2997,s=1508&a=21992,00.asp) included in Windows XP only protects you from incoming attacks, if you have installed some software that reports your actions back to the mothership then it will still be able to do that, ICF does nothing to prevent outgoing traffic. You might want to consider installing something like ZoneAlarm (http://www.zonealarm.com/) which will prevent outgoing traffic as well.
Assuming you have a firewall and are running an OS/2 machine as your gateway to the internet, you are ready to find out your vulnerabilities. To do this, you need to run a utility on your gateway machine that is just chock-full of interesting information about your TCP/IP stack.
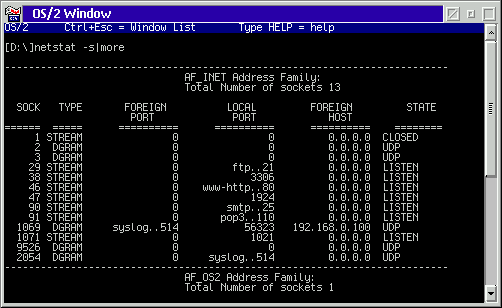
This is the output on my local web/mail/ftp serving machine. For the purpose of securing our machine from intruders, we're most interested in the LOCAL PORT column. This shows which ports are in use on our machine and if possible, lists the services that those ports provide.
If you have ports you are unsure about, open \mptn\etc\services. This file lists many of the common internet services and the port numbers assigned to them. Three ports to particularly watch out for are 137-139. These are the ports used by NetBios over TCP/IP, and if they are open to the outside world, it is pretty much a wide open door for crackers to muck with your system.
The way I always configure a firewall is to block everything by default, and then specifically allow access only to the ports needed by the applications I am running. This way you are better protected from security leaks when you install new software.
I should also mention that there are two types of ports, UDP and TCP. Firewalls can selectively block either type, and you can see what sort of port a given service uses by looking in the \mptn\etc\services file. Some services use TCP only, some use UDP only, and others use both. You should be sure to only allow access to the port and port type used by the specified service you want to pass through the firewall. If a service only uses one type of port, such as UDP, it is quite likely that the other type of port may be used by another service that you don't want to be able to pass through freely.
NAT or Network Address Translation is a facility built into most firewalls which causes the firewall to make all the computers on a LAN look like one single computer as far as anyone on the outside is concerned. It is the NAT engine's responsibility to make sure that when a computer on your LAN requests a web page that the resulting web page ends up getting back to the computer that requested it in the first place. This allows you to connect more than one computer to the internet through a single internet IP address.
In general, as long as you are using private network addresses (like 192.168.0.x or 10.x.x.x) on your LAN, you don't have to worry about anyone cracking into your machine (other than the gateway/firewall machine) from the outside world. So even if some cracker fakes up such an address and sends it to your gateway, these addresses are not routable, so they should be stopped by the NAT engine or the firewall.
What you may have to worry about is software that transmits information to the internet, for example reporting your music preferences, the files you have downloaded, the DVD's you've watched, or the websites you prefer. Often these programs misuse standard internet port numbers so that they can sneak past firewalls. Fortunately, these are mainly the domain of Windows computers, but if you're running a family network, chances are good you have at least one of these malware magnets around. If you have a Windows PC, you should look at ZoneAlarm (http://www.zonealarm.com/) for preventing unauthorized outgoing traffic and at AdAware (http://www.lavasoftusa.com/aaw.html) for removing any spyware applications you may have picked up. I am particularly careful about spyware, but a recent AdAware scan on my Windows machine turned up a couple of nasties.
 Robert Basler is the president of
Aurora Systems, Inc. (http://www.aurora-systems.com)
and has been a dedicated OS/2 user since he tired of rebooting Windows 3.1 twenty times a day.
He spends what free time he can manage travelling the world. Photo was taken at Franz Josef
glacier, New Zealand.
Robert Basler is the president of
Aurora Systems, Inc. (http://www.aurora-systems.com)
and has been a dedicated OS/2 user since he tired of rebooting Windows 3.1 twenty times a day.
He spends what free time he can manage travelling the world. Photo was taken at Franz Josef
glacier, New Zealand.
This article is courtesy of www.os2ezine.com. You can view it online at http://www.os2ezine.com/20020516/page_6.html.